
Cyber attacks: do we need another Greta for a global risk?
March
2019
In Italy, over 1500 serious attacks in 2018
The major attacks that were registered were 1552: 38% more attacks than in 2017, bringing the total number of attacks from 2011 to 8400 cases. The attacks also reached a greater level of severity, with greater consequences and damages. Cybercrime, computer-oriented crime committed against individuals or companies through identity and data theft, is now considered a lower degree of threat yet still being the main reason of attacks¬: 80% belongs to this category.
Cyberwar and Cyberespionage: threat levels rise
What makes the threat higher? The so-called Cyberwar, the ability of international governments of using technological tools and attacks to make pressure against other countries without an explicit dangerous exposure. Data confirms that this phenomenon is represented in small numbers but the size of the single attacks is huge. Instead, in recent years, cyber espionage and sabotage activities have widely spread, from “Fake news” campaigns to infiltrations for the theft of information in order to prepare political or economic attacks. In this regard, there is a growing number of attacks against the IT systems of government institutions, or their contractors or advisors, as well as a growing number of infrastructures of critical importance for a country.
“Industrial” actions: “multiple targets” attacks
However, the evolution of the subjects involved in cyber attacks has led to prefer large-scale actions with an approach that is defined as industrial, aiming at several objectives simultaneously: for this reason, the so-called "multiple targets" category is, according to the Clusit 2019 report, the main category of attacks, representing a fifth of the overall attacks registered, more than in the Government, Healthcare and Financial-Banking categories. From a geographical point of view, excluding multiple targets attacks that cross national borders, the victims of cyber operations are mostly to be found in the US area, especially in the Government and Healthcare categories.
Clusit: “simple” attack techniques are still very effective
An alarming factor that emerges from the Clusit report is how the use of predictable and well-known attack techniques is still very effective: 62% of serious attacks are carried out still using methods such as SQLi, DDos, Phishing and simple malware with a low degree of sophistication and overall low costs. On the other hand, however, the cyber crime industry develops and, alongside the predominance of malware, the category of attacks that have occurred with unknown tools is expanding.
Malware, the most wide spread and most expensive technique for victims
According to Accenture's annual study on the costs of cybersecurity, for organizations, malware cases are also the most expensive to resolve: 2.6 million dollars is the quantification made by collecting information from over 350 companies belonging to 16 industrial sectors in 11 countries. The amount is mainly made up of damages caused by the loss of relevant information. This ends up in raising the estimated economic impacts ($ 2.3 million) for an organization that is victim of web-based cyber attacks, that rank in second place.
Identity and access authentication: an effective best practice
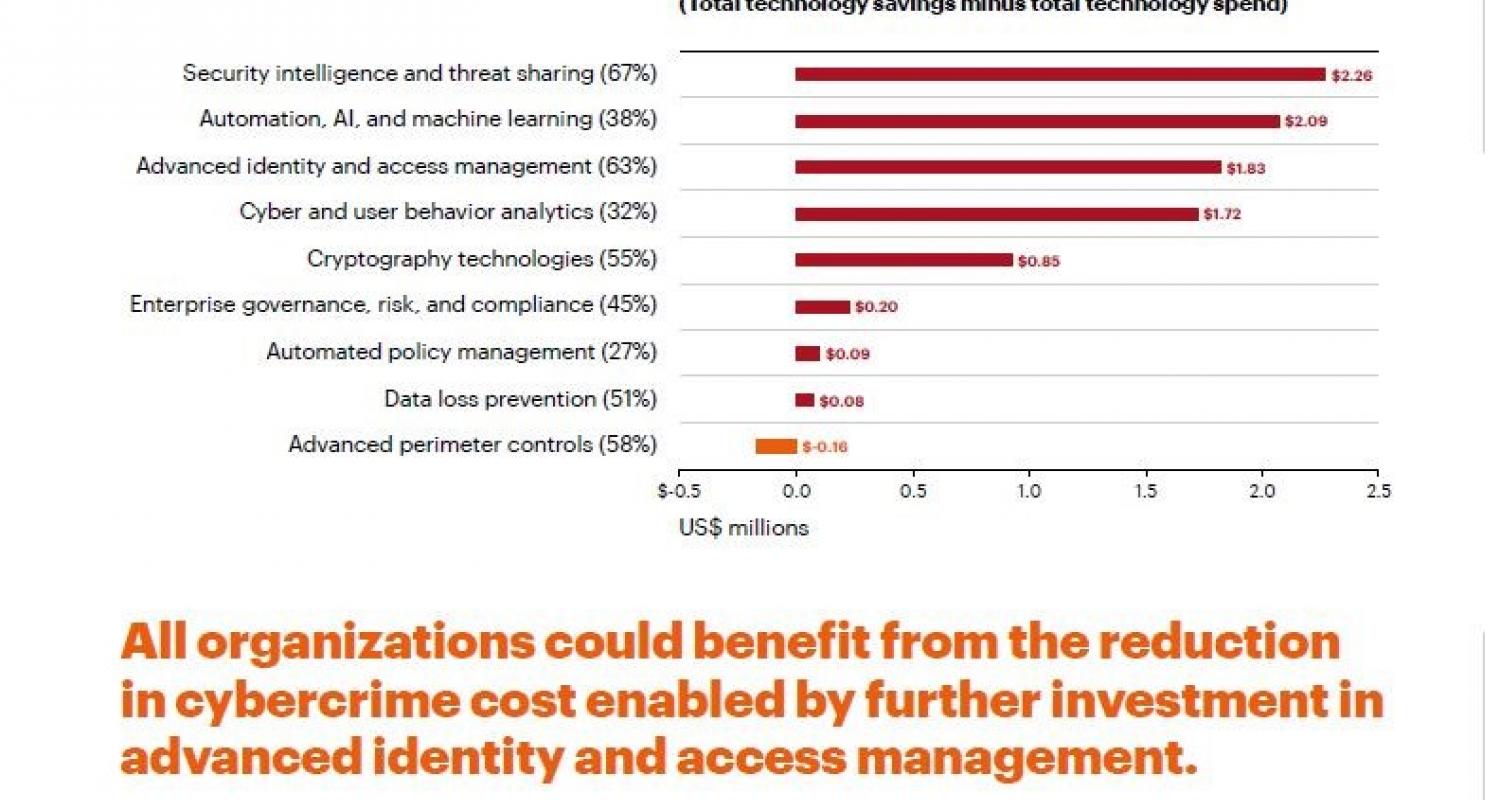
The Ninth Annual Cost of Cybercrime Study from Accenture, in addition to describing in detail the costs that businesses face after a cyber attack in terms of economic (and reputational) damage, also describes which technologies are currently being targeted and/or should be targeted more, in order to safeguard business and reputation.
The Net technology savings graph (shown below), in other words, the technologies that can protect against certain types of attacks and save companies and institutions a lot of money, shows how "Advanced identity and Access management", that is, authentication, secure monitoring and management of users and accesses are ranked in third place. This means that, although already widely used by 63% of the more than 2000 companies interviewed, analysts see in the major investments in this area not only an evident best practice to encourage in each company, but one of the most strategic territories on which they recommend to increase attention and resources. This applies within an organization for all users/employees in order to simplify the validation procedures of their identity, but it is even more crucial for a secure authentication procedure and protected access management when it comes to external solutions, such as platforms that require a secure user registration to manage projects and deals.
Business and security: when the web is crucial for finacial agreements
Despite the fears and threats of being cyber attacked or defrauded of one's identity, most of today’s delicate and complex operations are carried out almost entirely on the web. In business, particularly in finance, major operations such as mergers between companies, the acquisition of a competitor or a partner, or listing on the stock exchange, are all carried out on digital platforms to conduct the due diligence and negotiations and define the deal. This is why services such as secure and flexible virtual data rooms are being more and more used by companies, professional firms, institutions so much so that recent studies by Gartner estimate an average growth in double digits for the VDR market in the coming years, in terms of global turnover. As guardians of highly sensitive personal and corporate data, to ensure protection and security, VDRs rely heavily on user authentication (including two-factor authentication) and on granular permissions given to the users that are invited to enter the data room. This ensures complete traceability of the activities carried out by each user: all documents viewed are marked with a dynamic watermark showing the information of the user who has viewed it. The safest platforms also apply control and protection of data by design. Therefore, everything starts well before the login onto the platform, already in the choice of the IT architecture to be adopted (by the provider) on the single files (protection/segregation criteria with regards to viewing, printing and download) for each user or groups of users. The possibility to modify/revoke user permissions in the data room in any moment, makes monitoring and control over activities and data simple and fast.





